 In August 2009, a speeding Lexus with a stuck gas pedal crashed in San Diego, killing all four people aboard and spurring the ill-coneived theory that Toyota’s electronic controls were bugged. They weren’t. But as cars become rolling, autonomous supercomputers, what’s to stop an enterprising hacker from taking control of some functions, or causing a serious accident?
In August 2009, a speeding Lexus with a stuck gas pedal crashed in San Diego, killing all four people aboard and spurring the ill-coneived theory that Toyota’s electronic controls were bugged. They weren’t. But as cars become rolling, autonomous supercomputers, what’s to stop an enterprising hacker from taking control of some functions, or causing a serious accident?That’s the premise behind a new white paper written by Charlie Miller and Chris Valasek, the software engineers who successfully took over a Toyota Prius and Ford Escape last year to demonstrate how a modern car’s steering, brakes, and other primary controls could be compromised. Miller, a security researcher at Twitter, and Valasek, a director at computer security firm IOActive, aren’t ripping apart dashboards and causing havoc from a laptop as they did before. Their new paper, which they claim is the first security analysis of in-car networks, looks at the potential for 20 mostly late-model cars to be harmed by remote wireless attacks.
Before we digest the report (you can read it in its entirety here), understand that Miller and Valasek didn’t actually break into any of these cars. They also don’t have any insight, beyond schematics released on certain automaker-hosted service websites, of how the auto companies’ proprietary internal networks and ECUs specifically function. Still, that didn’t stop them from listing the three “most hackable” (2014 Jeep Cherokee, 2015 Cadillac Escalade, 2014 Infiniti Q50) and “least hackable” (2014 Dodge/SRT Viper, 2014 Audi A8, and 2014 Honda Accord) cars in their study. Nissan and Chrysler are reportedly investigating the findings. But ignoring their unproven assumptions about hackability, the duo discuss plenty of valid scenarios for potentially accessing a car’s systems. Automakers, lacking concrete answers and likely just as curious as we were when we looked into the issue, would prefer no one mention it.
While taking over a car’s physical controls remotely is extraordinarily difficult—a recent hackathon dedicated to cracking a Tesla Model S ended up operating lights and horns—Miller and Valasek point to active safety and telematics systems that are already programmed to brake, steer, and unlock the doors, as well as perform a host of other critical tasks. If these computers can be fooled, it could be game over. The guys looked at possible ways a hacker could access these computers via a car’s many wireless connections: Bluetooth, cellular, Wi-Fi, web browser software, telematics ECUs, keyless ignitions, and anti-theft key codes. Even tire-pressure monitoring systems, which send short-range radio signals to a processor, and the Radio Data System, which downloads text information to identify radio stations and songs, were included.
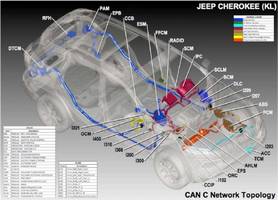
A CAN (controller area network) system as seen in a 2014 Jeep Cherokee.
Bluetooth was deemed “one of the biggest and most visible attack surfaces on the modern automobile” and could involve connecting surreptitiously with an unpaired phone. Telematics systems (“the holy grail”) are also at risk; in 2011, other hackers were able to upload malicious code to an OnStar-like system and then secretly record conversations in the car. Thirdly, internet browsers and apps were deemed to be problematic by being hack-prone in a similar fashion to desktop software. Says Miller and Valasek, “Complex code is being added to vehicles and there is no reason to believe corresponding anti-exploitation technologies are being added with them.”
--------------------
· Can Your Car Be Hacked? We Explore Six Ways (Including MP3 Music!)
· Tesla Model S Hackathon in China Turns Up Nothing More Sinister than Parlor Tricks
· Instrumented Test: 2014 Jeep Cherokee Trailhawk V-6
--------------------
That’s probably dead accurate. If anything, this paper will force automakers to have open conversations about data security and convince drivers they won’t be randomly brake-checked—or lose control over their own vehicles—on the highway. Still, auto engineers lock the dozens of computers in vehicles behind gateways and CAN bus networks, many of which are accessible only when dealers use specific automaker repair tools connected to an OBD port. What’s more, the general underlying structure is largely secret and highly guarded by automakers, even from their suppliers, for obvious reasons. But rapidly advancing technologies like drive-by-wire steering and autonomous driving could soon mean getting anti-virus updates with every oil change. Reported by Car and Driver 2 hours ago.